A big change happening in a lot of environments right now is the shift to enforcing the use of TLS 1.2 as your primary protocol provider. Standards with PCI compliance now require any site accepting credit card information for payments use TLS 1.2.
This is a complex topic so ensure you do your research and understand how the configuration of these settings present in an environment and whether your settings are secure. Additionally, security sensitive topics are always subject to change and I will try to keep this up to date.
Read More...
The configuration takes MANY things into consideration such as OS versions, hotfixes, .Net versions, and multiple registry keys. To simplify the tracking of your progress and identification of systems out of compliance I have created a Management Pack to assist you in this. This Management Pack will test each of the following items and ensure whether you are forcing TLS 1.2 on your monitored machines or not.
-
Testing Reg Key configurations to ensure neither Client or Server keys allow any unsecure protocols to be either Enabled or Negotiable.
- Testing TLS 1.2 Registry Key to ensure it is Enabled.
- Ensuring you are enforcing strong cryptography.
- Allowing applications to use the OS Default settings.
-
OPTIONALLY: I report in the discovery on the .Net Framework Version
-
A workflow can be enabled to generate alerts for versions below 4.6.2
- Having a .Net Version at or above this level can simplify your compliance configuration.
MP presentation in the Monitoring Pane
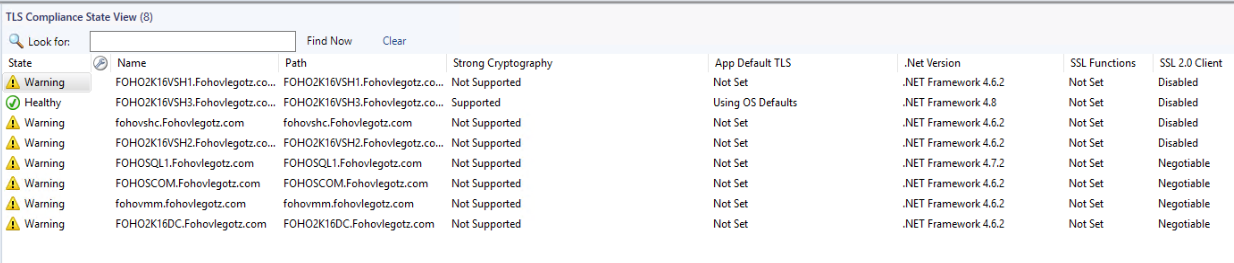
TLS Compliance State View – Displaying all configurations for discovered instances.

Generated alerts to notify recipients of devices out of Compliance.
As a cherry on top. This MP also has some discoveries and optional monitors to test configurations for secure Ciphers, Key Exchange Algorithms and Hashes as these can factor into your overall picture of compliance.

Cipher State View – Additionally a monitor can be enabled to check for secure configurations
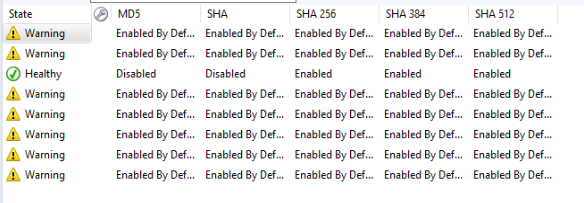
Hash State View – Additionally a monitor can be enabled to check for secure configurations
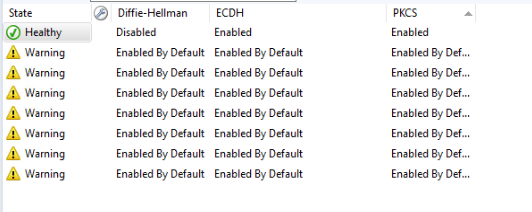
Key Exchange Algorithm State View
– – Additionally a monitor can be enabled to check for secure configurations
Lastly, a big thank you to a few individuals that help me put this together. Robin Kenny, Husam Hilal and the crew at MonitoringGuys.com. Without them this would not have been possible.